QUESTION 1
Which three options can a network administrator utilize by using PPP Layer 2 encapsulation?
(Choose three.)
A. authentication
B. VLAN support
C. compression
D. multilink support
Answer: A,C,D
QUESTION 2
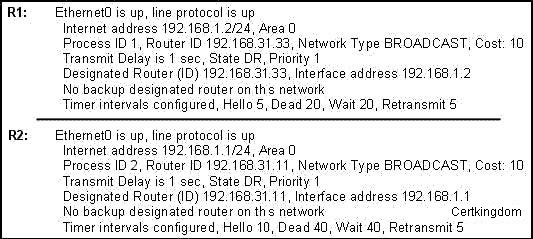
A network administrator is troubleshooting the OSPF configuration of routers R1 and R2. The
routers cannot establish an adjacency relationship on their common Ethernet link. The graphic
shows the output of the show ip ospf interface e0 command for routers R1 and R2. Based on the
information in the graphic, what is the cause of this problem?
A. The hello and dead timers are not configured properly.
B. The OSPF process ID numbers must match.
C. A backup designated router needs to be added to the network
D. The cost on R1 should be set higher.
Answer: A
Explanation:
As can be seen above, the hello interval for R1 has been set to 5 seconds, while it is set to 10 for
R2. Also, the dead interval on R1 is set at 20 seconds while on router CKD2 it is set to 40 seconds.
In order for two routers to establish an OSPF neigh adjacency, the hello and dead timers must
match.
QUESTION 3
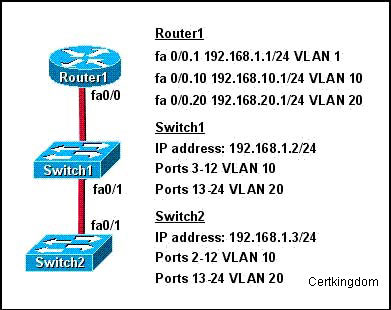
Refer to the exhibit. How should the FastEthernet0/1 ports on the 2950 model switches that are
shown in the exhibit be configured to allow connectivity between all devices?
A. The ports only need to be connected by a crossover cable.
B. SwitchX (config)# interface fastethernet 0/1
SwitchX (config-if)# switchport mode access
SwitchX (config-if)# switchport access vlan 1
C. SwitchX (config)# interface fastethernet 0/1
SwitchX (config-if)# switchport mode trunk
SwitchX (config-if)# switchport trunk vlan 1
SwitchX (config-if)# switchport trunk vlan 10
SwitchX (config-if)# switchport trunk vlan 20
D. SwitchX(config)# interface fastethernet 0/1
SwitchX(config-if)# switchport mode trunk
Answer: D
QUESTION 4
Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)# switchport port-security
2950Switch(config-if)# switchport port-security mac-address sticky
2950Switch(config-if)# switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when
this frame is received by 2950Switch? (Choose two.)
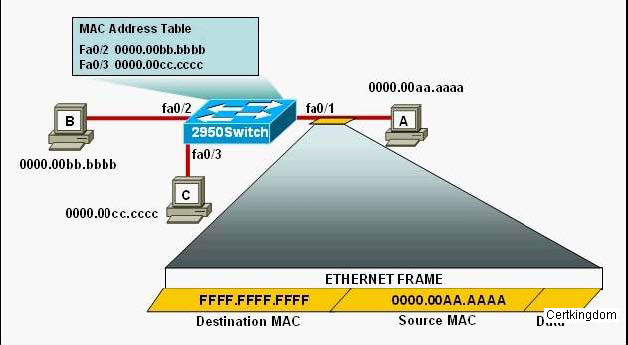
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. This frame will be discarded when it is received by2950Switch.
C. Only host A will be allowed to transmit frames on fa0/1.
D. All frames arriving on2950Switch with a destination of 0000.00aa.aaaa will be forwarded out
fa0/1.
Answer: C,D
Explanation:
The configuration shown here is an example of port security, specifically port security using sticky
addresses. You can use port security with dynamically learned and static MAC addresses to
restrict a port's ingress traffic by limiting the MAC addresses that are allowed to send traffic into
the port. When you assign secure MAC addresses to a secure port, the port does not forward
ingress traffic that has source addresses outside the group of defined addresses. If you limit the
number of secure MAC addresses to one and assign a single secure MAC address, the device
attached to that port has the full bandwidth of the port.
Port security with sticky MAC addresses provides many of the same benefits as port security with
static MAC addresses, but sticky MAC addresses can be learned dynamically. Port security with
sticky MAC addresses retains dynamically learned MAC addresses during a link-down condition.
If you enter a write memory or copy running- config startup- config command, then port security
with sticky MAC addresses saves dynamically learned MAC addresses in the startup- config file
and the port does not have to learn addresses from ingress traffic after bootup or a restart.
Since the maximum number of MAC addresses has been configured to 1, only host A will be able
to send frames on interface fa 0/1, making choice C correct.
QUESTION 5
A university has a small campus in which 25 faculty members are located. The faculty offices and
student computers are currently on the same network. The faculty are concerned about students
being able to capture packets going across the network and obtain sensitive material. In order to
protect faculty network traffic from student connections ,which action will you take?
A. Remove the student computers from the network and put them on a peer-to-peer network.
B. Put the faculty computers in a separate VLAN.
C. Power down the switches that connect to faculty computers when they are not in use.
D. Install anti-virus software on the student computers.
Answer: B
QUESTION 6
Running both IPv4 and IPv6 on a router simultaneously is known as dual-stack routing.
A. False
B. True
Answer: B
QUESTION 7
You are a network administrator. You configure a workgroup switch with all ports assigned to
VLAN 2. And you configure all ports as full-duplex FastEthernet. What is the effect of adding
switch ports to a new VLAN on this switch?
A. The additions will create more collisions domains.
B. IP address utilization will be more efficient.
C. The possibility that switching loops will occur will increase dramatically.
D. An additional broadcast domain will be created.
Answer: D
Explanation:
A VLAN is a group of hosts with a common set of requirements that communicate as if they were
attached to the same wire, regardless of their physical location. A VLAN has the same attributes
as a physical LAN, but it allows for end stations to be grouped together even if they are not located
on the same LAN segment.
Networks that use the campus-wide or end-to-end VLANs logically segment a switched network
based on the functions of an organization, project teams, or applications rather than on a physical
or geographical basis. For example, all workstations and servers used by a particular workgroup
can be connected to the same VLAN, regardless of their physical network connections or
interaction with other workgroups. Network reconfiguration can be done through software instead
of physically relocating devices.
Cisco recommends the use of local or geographic VLANs that segment the network based on IP
subnets. Each wiring closet switch is on its own VLAN or subnet and traffic between each switch is
routed by the router. The reasons for the Distribution Layer 3 switch and examples of a larger
network using both the campus-wide and local VLAN models will be discussed later.
A VLAN can be thought of as a broadcast domain that exists within a defined set of switches.
Ports on a switch can be grouped into VLANs in order to limit unicast , multicast, and broadcast
traffic flooding. Flooded traffic originating from a particular VLAN is only flooded out ports
belonging to that VLAN, including trunk ports, so a switch that connects to another switch will
normally introduce an additional broadcast domain.
QUESTION 8
Which technology helps prevent frames from looping continuously through this switched network?
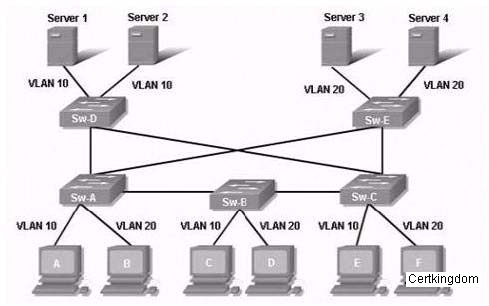
A. EIGRP
B. VTP
C. STP
D. ARP
Answer: C
QUESTION 9
What ports on Sw-AC3 are operating as trunks?(Choose three)
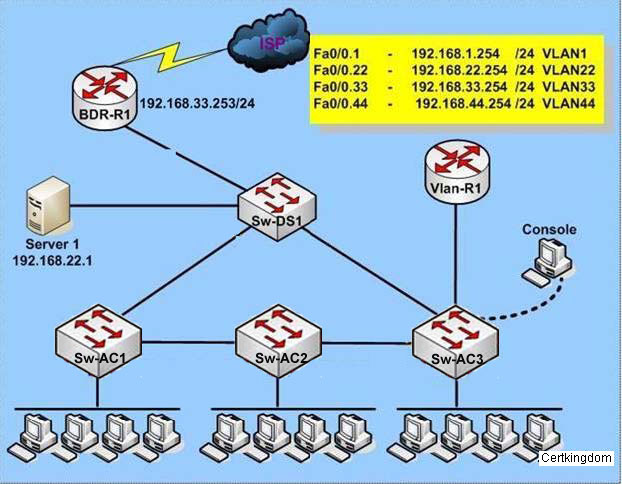
Sw-AC3#show int trunk
A. Fa0/1
B. Fa0/9
C. Fa0/12
D. Fa0/3
Answer: B,C,D
QUESTION 10
You are a network administrator. You want to add a line to an access list that will block only Telnet
access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. To accomplish this
task, what command should be used?
A. access-list 101 denyip 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B. access-list 1 denytcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
C. access-list 1 denytcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D. access-list 101 denytcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
Answer: D
Explanation:
Only choice specifies the correct TCT port and wildcard mask, and uses a valid access list
number.
Incorrect Answers:
A: IP is specified as the protocol, when it should be TCP.
B: Access list 1 is used for these choices, which is a standard access list. In this example, an
extended access list is required. Choice C also specifies port 21, which is used by FTP not Telnet.
C: Access list 1 is used for these choices, which is a standard access list. In this example, an
extended access list is required. Choice C also specifies port 21, which is used by FTP not Telnet.
QUESTION 11
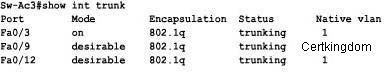
Refer to the exhibit. What will be the result of issuing the following commands?
Switch1(config)# interface fastethernet 0/5
Switch1(config-if)# switchport mode access
Switch1(config-if)# switchport access vlan 30
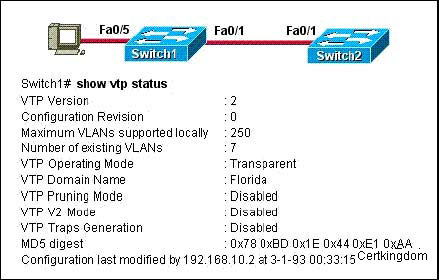
A. The VLAN will not be added to the database, but the VLAN 30 information will be passed on as
a VLAN to theSwitch2 VLAN database.
B. The VLAN will not be added to the database, nor will the VLAN 30 information be passed on as
a VLAN to theSwitch2 VLAN database.
C. The VLAN will be added to the database and VLAN 30 will be passed on as a VLAN to add to
theSwitch2 VLAN database.
D. The VLAN will be added to the database, but the VLAN information will not be passed on to
theSwitch2 VLAN database.
Answer: D
Explanation:
The three VTP modes are described below:
Server: This is the default for all Catalyst switches. You need at least one server in your VTP
domain to propagate VLAN information throughout the domain. The switch must be in server
mode to be able to create, add, or delete VLANs in a VTP domain. You must also change VTP
information in server mode, and any change you make to a switch in server mode will be
advertised to the entire VTP domain.
Client: In client mode, switches receive information from VTP servers; they also send and receive
updates, but they can't make any changes. Plus, none of the ports on a client switch can be added
to a new VLAN before the VTP server notifies the client switch of the new VLAN. Here's a hint: if
you want a switch to become a server, first make it a client so that it receives all the correct VLAN
information, then change it to a server-much easier!
Transparent: Switches in transparent mode don't participate in the VTP domain, but they'll still
forward VTP advertisements through any configured trunk links. These switches can't add and
delete VLANs because they keep their own database-one they do not share with other switches.
Transparent mode is really only considered locally significant.
In our example, the switch is configured for transparent mode. In transparent mode the local
VLAN information can be created but that VLAN information will not be advertised to the other
switch.
QUESTION 12
S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in the hub-andspoke
Frame Relay topology shown in the exhibit. Originally, static routes were configured
between these routers to successfully route traffic between the attached networks. What will need
to be done in order to use RIP v2 in place of the static routes?
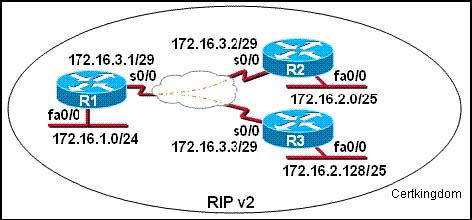
A. Change the 172.16.2.0/25 and 172.16.2.128/25subnetworks so that at least two bits are
borrowed from the last octet.
B. Configure the noip subnet-zero command on R1, R2, and R3.
C. Configure the s0/0 interface on R1 as two sub interfaces and configure point-to-point links toR2
and R3.
D. Dynamic routing protocols such as RIP v2 cannot be used across Frame Relay networks.
Answer: C
QUESTION 13
An access list has been designed to prevent HTTP traffic from the Accounting Department from
reaching the HR server attached to the Holyoke router. Which of the following access lists will
accomplish this task when grouped with the e0 interface on the Chicopee router?
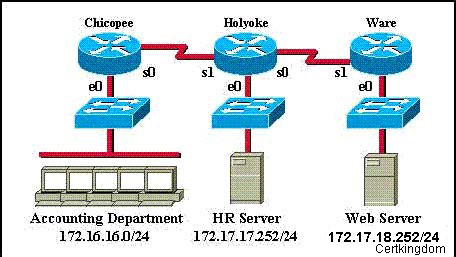
A. denytcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80 permit ip any any
B. permitip any any deny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80
C. permitip any any deny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80
D. denytcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80 permit ip any any
Answer: A
QUESTION 14
Which three benefits are of VLANs? (Choose three.)
A. They can enhance network security.
B. They allow logical grouping of users by function.
C. They simplify switch administration.
D. They increase the number of broadcast domains while decreasing the size of the broadcast
domains.
Answer: A,B,D
Explanation:
VLANs are used to segment a LAN into multiple, smaller LANs. This can be used to enhance
security as local traffic from one VLAN will not be passed to users in other VLANS.
QUESTION 15
A network administrator would configure port security on a switch, why?
A. to prevent unauthorized Telnet from accessing to a switch port
B. to protect the IP and MAC address of the switch and associated ports
C. to prevent unauthorized hosts from accessing the LAN
D. to block unauthorized access to the switch management interfaces over common TCP ports
Answer: C
Explanation:
You can use the port security feature to restrict input to an interface by limiting and identifying
MAC addresses of the stations allowed to access the port. When you assign secure MAC
addresses to a secure port, the port does not forward packets with source addresses outside the
group of defined addresses. If you limit the number of secure MAC addresses to one and assign a
single secure MAC address, the workstation attached to that port is assured the full bandwidth of
the port.
If a port is configured as a secure port and the maximum number of secure MAC addresses is
reached, when the MAC address of a station attempting to access the port is different from any of
the identified secure MAC addresses, a security violation occurs. Also, if a station with a secure
MAC address configured or learned on one secure port attempts to access another secure port, a
violation is flagged.
Reference:
http://www.cisco.com/en/US/products/hw/switches/ps628/products_configuration_guide_chapter0
9186a00800d6a38.html#86378

